Hello, friends! Did you know your passwords might already be floating around on the dark web? We’re not kidding—this is serious. A recent investigation by cyberattack revealed one of the largest data breaches in history, with over 16 billion login credentials exposed online. These include Apple, Google, Facebook, and Instagram accounts.
While some experts argue that the number may be inflated due to repeated data from past leaks, the threat is real. Hackers can use leaked passwords to steal your identity, access financial accounts, blackmail you, or sell your personal data.
So the big questions are:
- How do you create a password that hackers can’t crack?
- How do you know if your password has been leaked?
- What steps can you take to secure your accounts now?
Four main hacker methods to steal passwords
It is very important in today’s digital world. Especially for your parents and the elders in your family. Almost everyone uses smartphones these days. But not everyone knows about these precautions. So, show this article to your friends and the elders in your family. Broadly speaking, there are four main ways used by hackers and cyber criminals to steal your passwords. The first and most common way is Phishing. In this, hackers try to trick you through emails, WhatsApp messages, or SMSs, trying to convince you to reveal your password.
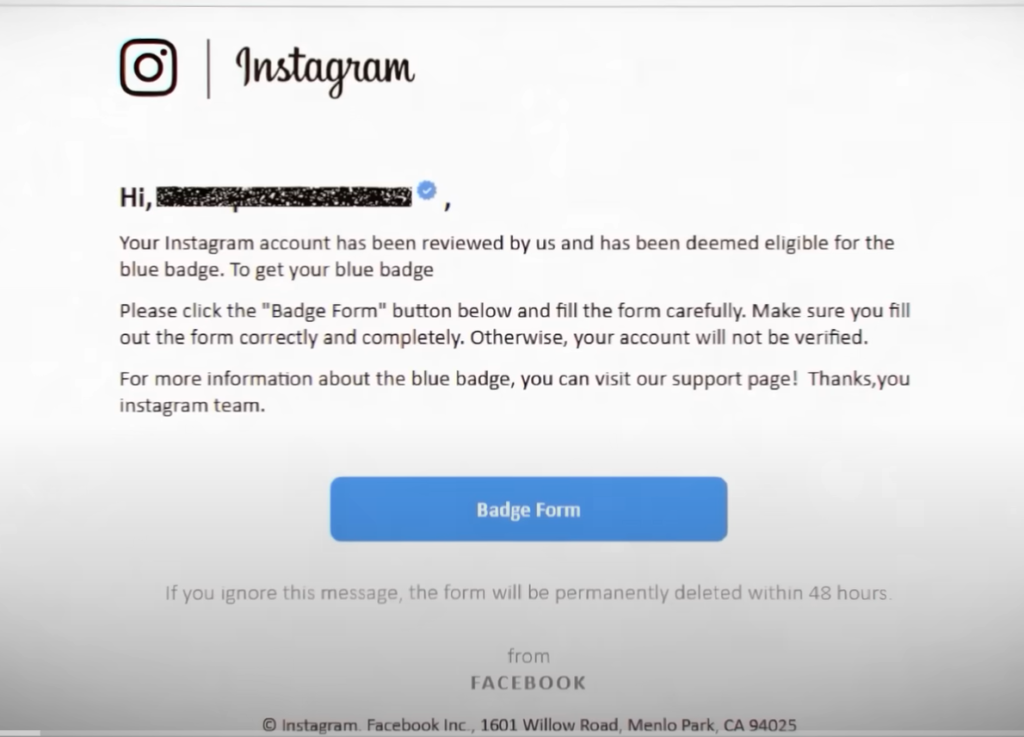
You might be thinking, How is this possible? You must have seen such emails in your spam folder. Email from ‘Facebook’ or ‘Instagram’. Offering you the blue tick. Asking you to just click on the given button and add your details. And then you’ll get the blue tick. This is a common example of a Phishing email. This email was not sent by Facebook or Instagram. Instead, it was sent by a hacker. But the email is presented as if it were sent by Facebook or Instagram. When you click on the button, you are asked to enter your information on a webpage,
It looks like you are logging in to your Facebook or Instagram account. But actually, that webpage is fake. And when you enter your username and password while logging in, that information goes to the hacker. Similarly, you might get SMSs on your phone that claim to be from the SBI. Informing you that your bank account has been temporarily suspended. Asking you to log in immediately. There’s a link too, such as www.online-sbi.com. Once again, it might feel like SBI’s website URL, but it’s not.
It looks like you are logging in to your Facebook or Instagram account. But actually, that webpage is fake. And when you enter your username and password while logging in, that information goes to the hacker. Similarly, you might get SMSs on your phone that claim to be from the SBI. Informing you that your bank account has been temporarily suspended. Asking you to log in immediately. There’s a link too, such as www.online-sbi.com. Once again, it might feel like SBI’s website URL, but it’s not.
There are minor differences in the names or URLs of these websites to differentiate them from the real website. But it might be difficult for a person to spot the differences on the webpage. You might enter your username and password innocently, while all your bank details and access to the bank account are shared with the hacker. Phishing is based on psychological manipulation. You share your information with the hacker unknowingly. The simple way to avoid this is to never log in by using the link from any email, SMS, or WhatsApp link.
credential stuffing
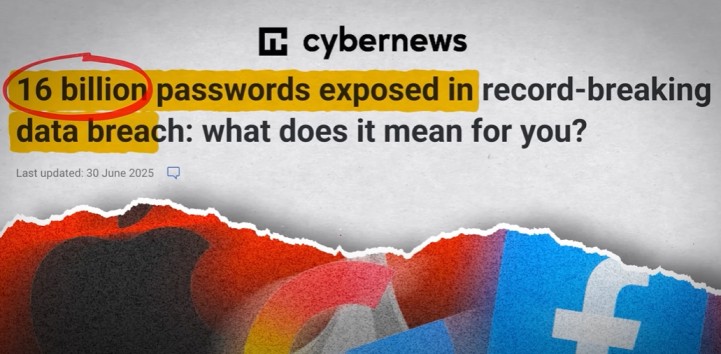
In it, the hackers use past data leaks. Like this news about 16 billion leaked passwords. The hackers found out about the major data breach. If you think that only your Instagram account’s data has been leaked, which might be pretty useless to you, because you never use it, so you may think that you are safe. But the hackers will look at the username and password combination.
And will try to access various websites using it. They can see your Instagram account’s leaked data. But you might use the same password on Facebook, Apple, or Google. Even if you don’t use the exact same password, you might be using somewhat similar passwords. This is called credential stuffing. ‘Stuff’ your leaked credentials on different websites to see if it works. They try to guess. And in most cases, it works. Because often, when people create accounts, they use the same username and password on different websites.
Password spraying attack technique

Password Spraying. In this technique, hackers try to test common passwords for many usernames. This technique is more successful than the previous one. Because today, most systems temporarily lock the account after a few failed login attempts. But with password spraying, hackers try to log into an account only once or twice. For example, let’s say a hacker has a list of 500 email IDs of government employees. Like abc@gov.in, cde@gov.in, xyz@gov.in. These are the email IDs of 500 different people. Now, hackers will use a common password on all of them. It can be any type of common password. For example, India@123. This is a common password used by many Indians. So, out of these 500 people, there might be a few who used this password.
Those who did, their accounts would be easily accessed by the hackers. The technique is special because there was no need for phishing or a data leak. These accounts were hacked with simple trial and error. Only because some people use extremely common passwords. The fourth method is brute force. In it, hackers try as many combinations of different passwords as they can. You’ve seen or may even have used these suitcases. It comes with a small lock, With a 3-digit key. Have you ever wondered how infallible these 3 digits can be?
if your password is short. If you use a 4-digit password, it can be breached almost immediately. It’s a bit more difficult with 5-digit, a bit more for 6-digit, the longer your password is, the more difficult it is for the computer software to try every combination. Now the question is, how can you avoid this? Because you won’t use a 100-digits-long password. Because the longer the password, the more difficult it will be to remember and use.
Common weak passwords and risks
Who use even weaker passwords. If we look at the top 10 most common passwords used in India, the one most used is 123456 second is the word ‘password’ third is 12345678 you can see the other common passwords too, at the 9th spot is the password I mentioned before, india123. If you are using any of these passwords, there’s a high chance that your inbox is full of phishing emails.
Common password patterns and vulnerabilities
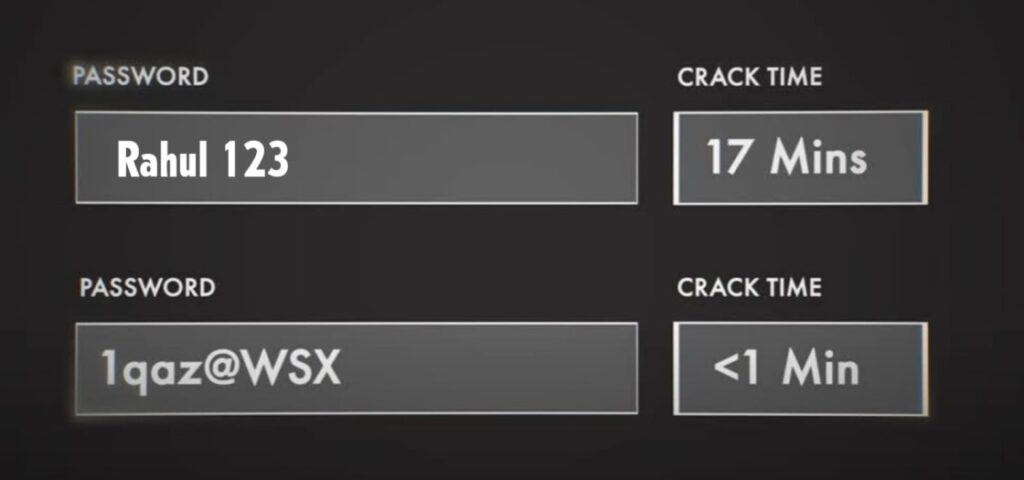
It uses alphabets, number, and even a symbol. How is this possible? There is a simple reason, friends. When hackers choose to use brute force, first, they look up the most common passwords online. If they are going to use brute force, or password spraying, they begin by trying these common passwords with different user accounts. So even though the entropy of a password might be higher,
Check data breaches with HaveIBeenPwned
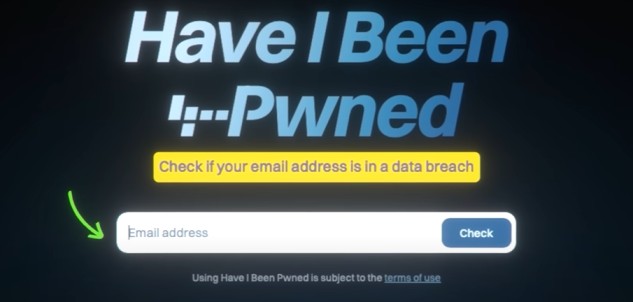
Now, a final question that you might have is, how can you check whether or not your account was hacked in these data leaks. For this, you can use this website. haveibeenpwned.com You can check your email id on this website whether your email id and its corresponding password has been leaked online or not. Don’t worry, I am not asking you to enter your password here. You have to enter your email ID only. Once you enter your email ID, you will see the history of the past data leaks where the login info and password associated with the email ID was leaked. For example, if I check the email ID narendramodi1234@gmail.com, which, according to some new websites is PM Modi’s actual gmail id, you will get the entire email breach history where this email id was included in 13 data breaches.
With the latest being this Alien Txt Base Stealer Logs. And as you scroll down, you will see that at different times, when different websites faced data leaks, for example, the Twitter data leak in January 2021 that affected more than 200 million user accounts, it mentions the compromised data too, email addresses, names, social media profiles and the username. Similarly, if you scroll further, you will see Bitly’s data leak in May 2014.
But remember one thing, after reading this blog, the first thing you need to do, is go change the password of all your important accounts. This is for your safety and security.

